Auth Key Cracked.to
VPN use is to be controlled using either a one-time password authentication, such as a token device, or a public/private key system with a strong passphrase. When actively connected to the corporate network, VPNs force all traffic to and from the PC over the VPN tunnel; all other traffic is dropped.
Cracked.to Auth Key FREE by MelloX - 28 November, 2020 - 09:03 AM. This post is by a banned member (MelloX) - Unhide. Members who are VIP, Pearl or Amber members always get their Auth Key and don't need to worry about any requirements. Simply purchase an Upgrade of your choice on Cracked.to and you are ready to use any tool. I get a message that my Key is invalid. › Cracked to auth key › Cracked to combolist. Hackers hack hackers: Cracked.to’s Giant Database Breached. Blog.koddos.net DA: 15 PA: 50 MOZ Rank: 65. Data and information of over 321,000 members of Cracked.to were exposed to dozens of hackers, endangering the.
Cracked to auth key keyword after analyzing the system lists the list of keywords related and the list of websites with related content, in addition you can see which keywords most interested customers on the this website
Keyword Suggestions
Most Searched Keywords
Domains Actived Recently
› Bbs.duomiluntan.com
› Crowsheathfishery.com
› Farrell-ryan.com
› Hire-a-car-australia.com
› M.visitmadison.org
› Na.industrial.panasonic.com
› Pythongeeks.org
› Sobhiran.com.pagesstudy.com
› Thispointer.com
Websites Listing
We found at least 10 Websites Listing below when search with cracked to auth key on Search Engine
› Cracked email accounts
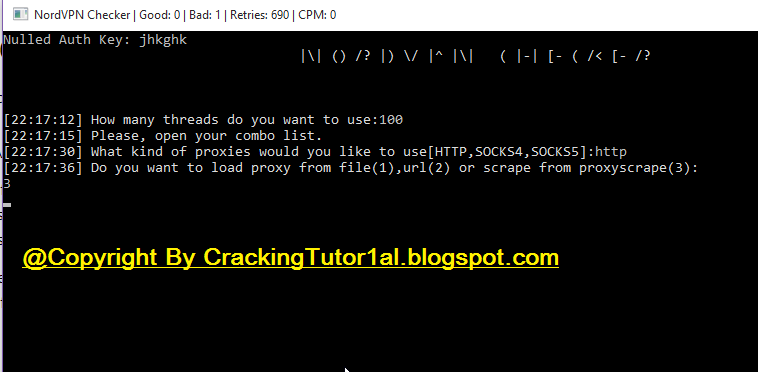
How to add Auth key in Checker (Cracked.to)
Youtube.comDA: 15PA: 6MOZ Rank: 21
Hello this is my tutorial on How to add Auth key in Checker (Cracked.to)Link for Code: https://cracked.to/Thread-C-Python-Cracked-to-Authentication-System-D
How to crack 95% of Nulled Auth Key Paid Tools
Youtube.comDA: 15PA: 6MOZ Rank: 22
Want to support me? Feel free to donate(Only if you wish!)!- https://www.paypal.me/AdarshChordia🛒BUY FROM MY UPDATED SHOP ! YOU'll Get DISCOUNTS ON MANY ITE
MRT Key Ver 3.19 Crack Tool With Free Key Generator
Gsmfirmware.netDA: 19PA: 41MOZ Rank: 62
- First, you need to download the desired program and key generator from the link below
- When you download it, turn off the antivirus and defender from the computer system, and then extract the compressed files of MRT Crack Tool and Key generator
- Run the loader ' Loader_MRT-Key.exe ' file, as soon as you run it, a hardware ID will appear, copy
Cracked.to auth key Cracked.to
Cracked.toDA: 10PA: 35MOZ Rank: 48
- This post is by a banned member (Tutifruti) - Unhide
How to Crack Any Software Key Serial Key Activation
Youtube.comDA: 15PA: 6MOZ Rank: 25
- Hello viewers! Today i'll show you how to crack any software activation key/serial key/ license key
- So lets do these steps and crack any software activation
Cracked to auth key' Keyword Found Websites Listing
Keyword-suggest-tool.comDA: 28PA: 28MOZ Rank: 61
- Selling Auth Key For (Cracked.to) Sinister.ly DA: 11 PA: 39 MOZ Rank: 53
- Let me guess, you want to use a app from cracked but you don't have the AUTH key! Well, your in damn luck, I have the AUTH key
- And I'm selling it for (4.99$-VIA PAYPAL) Just for 4.99$ you will get the AUTH key…
Cracked.to-Authentication/Auth.cs at master · Skryptific
Github.comDA: 10PA: 50MOZ Rank: 66
- Class library for Cracked.to's official authentication system written in C#
- - Skryptific/Cracked.to-Authentication
How to skip Auth Key in Fortnite Keker
Youtube.comDA: 15PA: 6MOZ Rank: 28
Checker LINK : https://mega.nz/?fbclid=IwAR2jy3T-aAtxCbHcUFZSqDFBoxpa0Kk7Zof2oUm3N0N2NegeKt5vlzX7heQ#F!amgkFCAJ!pvy8WNieXKu5XBdtJtK5hg
JAWS 2021.2102.34 Crack Latest Version Authorization
In.pinterest.comDA: 16PA: 24MOZ Rank: 48
- Jaws 2021.2102.34 Crack is the screen reading and speaking for blind people
- Get JAWS with Authorization Number & License key (2021)
Selling Auth Key For (Cracked.to)
Sinister.lyDA: 11PA: 39MOZ Rank: 59
- Selling Auth Key For (Cracked.to) 02-22-2019, 11:51 AM #1
- Let me guess, you want to use a app from cracked but you don't have the AUTH key! Well, your in damn luck, I have the AUTH key
- And I'm selling it for (4.99$-VIA PAYPAL)
How To Crack A Program Using OllyDBG Cracking A Program
Wayofthecracker.wordpress.comDA: 29PA: 50MOZ Rank: 89
Cracked.to Auth Key
- This entry was posted in The Roads To The End and tagged A, crack, crack a program to get serial key, how, how to crack a program, how to crack a program using ollydbg, ollydbg, program, to, tutorial, using on August 31, 2012 by ShowerTales!
Free my band: Mi Band 6 / Mi Band 5 / Mi Band 4 Auth key
Freemyband.comDA: 18PA: 32MOZ Rank: 61
- Mi Band 6 / Mi Band 5 / Mi Band 4 Auth key
- In few simple steps you can get your Mi Band 4 / Mi Band 5 / Mi Band 6 Auth key to connect any app
- 1) Unpair band from existing official app
- 3) Reset your Mi Band (optional) 4) Download and install the Mi Fit mod apk version
Cracking NETLM/NETNTLMv1 Authentication crack.sh
Crack.shDA: 8PA: 9MOZ Rank: 29
- 100% Success Guarantee Crack.sh guarantees that it will 100% produce a working key for jobs submitted
- If for some reason a key isn't found, crack.sh will immediately refund your payment, fix any problem in its system that made it not find the key, and deliver the key to you once it's fixed.
Ssh-keygen is a tool for creating new authentication key
Ssh.comDA: 11PA: 19MOZ Rank: 43
- The authentication keys, called SSH keys, are created using the keygen program
- SSH introduced public key authentication as a more secure alternative to the older .rhosts authentication
- It improved security by avoiding the need to have password stored in files, and eliminated the possibility of a compromised server stealing the user's password.
Cisco Type 7 Password Decrypt / Decoder / Cracker Tool
Firewall.cxDA: 15PA: 50MOZ Rank: 79
- Cisco type 7 password decrypt hack crack
- This page allows users to reveal Cisco Type 7 encrypted passwords
- authentication open authentication key-management wpa guest-mode mbssid guest-mode infrastructure-ssid optional wpa-psk ascii 7 01150F165E1C07032D.
How To Generate SSH Key With ssh-keygen In Linux
Geeksforgeeks.orgDA: 21PA: 50MOZ Rank: 86
- Ssh-keygen is the utility used to generate, manage, and convert authentication keys for SSH
- Ssh-keygen comes installed with SSH in most of the operating systems
- Ssh-keygen is able to generate a key using one of three different digital signature algorithms.
Toad Software: Toad Authorization Key Generator
Toadsoftware.blogspot.comDA: 25PA: 46MOZ Rank: 87
- Toad Authorization Key Generator is a software used to generate Authorization Key according to Site Message for various Toad Software
- If you are well known about Toad Authorization Key Generator and want to download the software, you can just skip this boring text and follow the link: Toad Authorization Key Generator Take a look of software screenshot.
10 examples to generate SSH key in Linux (ssh-keygen
Golinuxcloud.comDA: 20PA: 24MOZ Rank: 61
- We use ssh-keygen tool to generate SSH keys which are used for Public Key Based Authentication with SSH
- As the time of writing this article, there are 6 different types of authentication methods possible with SSH.But Public key Authentication is one of the most used authentication methods used across production environment.
- To use public key based authentication you would need a public …
How to secure your SSH server with public key Ed25519
Cryptsus.comDA: 12PA: 50MOZ Rank: 80
- SSH can generate DSA, RSA, ECDSA and Ed25519 key pairs
- Let's go over these public-key algorithms: DSA: This algorithm is deprecated due to very poor randomness
- OpenSSH version 7.0 and newer even refuse DSA keys smaller than 1024-bits
- DSA key pairs should not be used anymore
- RSA: This non-elliptic crypto algorithm which is based on prime
Using ssh-keygen and sharing for key-based authentication
Redhat.comDA: 14PA: 30MOZ Rank: 63
- The other method is to password-protect your private key so that you are prompted for the password when authenticating (think two-factor authentication using both the private key and the password)
- To generate an SSH key pair, use the following command: [[email protected] ~]$ ssh-keygen Generating public/private rsa key pair.
How To Configure SSH Key-Based Authentication on a Linux
Nulled Auth Key
Digitalocean.comDA: 20PA: 50MOZ Rank: 90
- The first step to configure SSH key authentication to your server is to generate an SSH key pair on your local computer
- To do this, we can use a special utility called ssh-keygen, which is included with the standard OpenSSH suite of tools
- By default, this will create a 3072 bit RSA key pair.
Generate the VM Auth Key on Panorama
Docs.paloaltonetworks.comDA: 25PA: 50MOZ Rank: 96
- The VM auth key allows Panorama to authenticate the newly bootstrapped VM-Series firewall
- So, to manage the firewall using Panorama, you must include the IP address for Panorama and the VM auth key in the basic configuration file as well as the license auth codes in the /license folder of the bootstrap package.
Configure 'No Password SSH Keys Authentication' with PuTTY
Tecmint.comDA: 15PA: 35MOZ Rank: 72
- In order to automatically connect and login to your server you need to add the Private Key to Putty client
- Open Putty and add your server login user followed by your server IP Address or FQDN on Host Name field in the form of [email protected], enter your server SSH Port number if it was changed.
- Then go to left Category menu, select SSH –> Auth, hit the Browse
How to revoke specific key used to login with OpenSSH
Sleeplessbeastie.euDA: 19PA: 50MOZ Rank: 92
- Revoke specific key used to perform key-based login with OpenSSH utilizing simple public key revocation list or OpenSSH Key Revocation List (KRL)
- OpenSSH configuration Create empty revocation list file.
SSH Public key authentication or password less
Unixutils.comDA: 13PA: 50MOZ Rank: 87
- The keys can be encrypted with RSA, DSA, ECDSA algorithms, by passing it with the ‘-t’ argument
- One can also specify the key size using the ‘-b’ argument
- Example: ssh-keygen -t rsa -b 4096 ssh-keygen -t dsa ssh-keygen -t ecdsa -b 521 ssh-keygen -t ed25519 Copying public key to remote systems
- Public key can be copied to remote system
OpenSSH key management for Windows Microsoft Docs
Docs.microsoft.comDA: 18PA: 50MOZ Rank: 93
- To use key-based authentication, you first need to generate public/private key pairs for your client
- Ssh-keygen.exe is used to generate key files and the algorithms DSA, RSA, ECDSA, or Ed25519 can be specified
- If no algorithm is specified, RSA is used
- A strong algorithm and key length should be used, such as Ed25519 in this example.
26.5.3 Using ssh-keygen to Generate Pairs of
Docs.oracle.comDA: 15PA: 50MOZ Rank: 91
Auth Key Cracked.to Go
- 26.5.3 Using ssh-keygen to Generate Pairs of Authentication Keys
- The ssh-keygen command generate a public and private authentication key pair
- Such authentication keys allow you to connect to a remote system without needing to supply a password each time that you connect
- Each user must generate their own pair of keys.
How to Add an SSH Key to VS Code and Connect to a Host
Adamtheautomator.comDA: 20PA: 24MOZ Rank: 71
- To begin, you’ll first need to generate a private and public SSH key on your Windows machine
- Open up PowerShell on your local computer and run ssh-keygen
- The default path for your keys is C:users<user>.ssh
- Provide the folder path to save the private and public key
- The default is C:Users<user>.sshid_rsa.
Delete SSH Keys Command for Linux and Unix
Cyberciti.bizDA: 17PA: 40MOZ Rank: 85
- A note about removing a particular host key from SSH’s known_hosts file Use the ssh-keygen command as follows ssh-keygen -R your-hostname ssh-keygen -R server1.cyberciti.biz
- DenyUsers option can block any user
- Another option is to edit the sshd_config file on your remove Unix or Linux server
- From the man page: DenyUsers option can block
14.2.4. Using Key-Based Authentication Red Hat Enterprise
Access.redhat.comDA: 17PA: 50MOZ Rank: 96
- To improve the system security even further, you can enforce key-based authentication by disabling the standard password authentication
- To do so, open the /etc/ssh/sshd_config configuration file in a text editor such as vi or nano , and change the PasswordAuthentication option as follows:
Configuring SSH Key-based Authentication on Ubuntu 20.04
Answertopia.comDA: 19PA: 50MOZ Rank: 99
- Press the Enter key to accept the default location for the key files
- This will place two files in the .ssh sub-directory of the current user’s home directory
- The private key will be stored in a file named id_rsa while the public key will reside in the file named id_rsa.pub.
- Next, ssh-keygen will prompt for a passphrase with which to protect the private key.
› Export linkedin contacts csv
› Physician jobs search
› Digital data release form
› The martin funeral home clanton
› Best wire for internet connection
› Upmc help desk password reset
Top